Itil Audit Checklist
An information technology audit, or information systems audit, is an examination of the management controls within an Information technology (IT) infrastructure. The evaluation of obtained evidence determines if the information systems are safeguarding assets, maintaining data integrity, and operating effectively to achieve the organization's goals or objectives. These reviews may be performed in conjunction with a financial statement audit, internal audit, or other form of attestation engagement.
IT audits are also known as automated data processing audits (ADP audits) and computer audits.
ITIL Assessment Report. September 14. Implement audit process. Document releases and the release procedures using a checklist. Book Review - Auditing Cloud Computing - ISACA. ITIL Financial Management using an Implementation Checklist. Financial Management - Implementation Checklist. It is also important to audit for any credibility gap between the value being received and price being paid as soon as possible. This can be done through providing. The Information Technology services management system - ISO 20000 certification documents that includes service management system plan, policies, procedures, sample plan, templates, forms, SOPs, job descriptions, iso 20000 audit checklist and more.
They were formerly called electronic data processing audits (EDP audits).
- 6Audit personnel
- 8Emerging issues
- 9See also
Purpose[edit]
An IT audit is different from a financial statement audit. While a financial audit's purpose is to evaluate whether the financial statements present fairly, in all material respects, an entity's financial position, resultsof operations, and cash flows in conformity to standard accounting practices, the purposes of an IT audit is to evaluate the system's internal control design and effectiveness. This includes, but is not limited to, efficiency and security protocols, development processes, and IT governance or oversight.Installing controls are necessary but not sufficient to provide adequate security. People responsible for security must consider if the controls are installed as intended, if they are effective, or if any breach in security has occurred and if so, what actions can be done to prevent future breaches. These inquiries must be answered by independent and unbiased observers. These observers are performing the task of information systems auditing. In an Information Systems (IS) environment, an audit is an examination of information systems, their inputs, outputs, and processing.[1]
The primary functions of an IT audit are to evaluate the systems that are in place to guard an organization's information. Specifically, information technology audits are used to evaluate the organization's ability to protect its information assets and to properly dispense information to authorized parties. The IT audit aims to evaluate the following:
Will the organization's computer systems be available for the business at all times when required? (known as availability)Will the information in the systems be disclosed only to authorized users? (known as security and confidentiality)Will the information provided by the system always be accurate, reliable, and timely? (measures the integrity)In this way, the audit hopes to assess the risk to the company's valuable asset (its information) and establish methods of minimizing those risks.
Types of IT audits[edit]
Various authorities have created differing taxonomies to distinguish the various types of IT audits. Goodman & Lawless state that there are three specific systematic approaches to carry out an IT audit:[2]
- Technological innovation process audit. This audit constructs a risk profile for existing and new projects. The audit will assess the length and depth of the company's experience in its chosen technologies, as well as its presence in relevant markets, the organization of each project, and the structure of the portion of the industry that deals with this project or product, organization and industry structure.
- Innovative comparison audit. This audit is an analysis of the innovative abilities of the company being audited, in comparison to its competitors. This requires examination of company's research and development facilities, as well as its track record in actually producing new products.
- Technological position audit: This audit reviews the technologies that the business currently has and that it needs to add. Technologies are characterized as being either 'base', 'key', 'pacing' or 'emerging'.
Others describe the spectrum of IT audits with five categories of audits:
Itil Audit Program
- Systems and Applications: An audit to verify that systems and applications are appropriate, are efficient, and are adequately controlled to ensure valid, reliable, timely, and secure input, processing, and output at all levels of a system's activity. System and process assurance audits form a subtype, focussing on business process-centric business IT systems. Such audits have the objective to assist financial auditors.[3]
- Information Processing Facilities: An audit to verify that the processing facility is controlled to ensure timely, accurate, and efficient processing of applications under normal and potentially disruptive conditions.
- Systems Development: An audit to verify that the systems under development meet the objectives of the organization, and to ensure that the systems are developed in accordance with generally accepted standards for systems development.
- Management of IT and Enterprise Architecture: An audit to verify that IT management has developed an organizational structure and procedures to ensure a controlled and efficient environment for information processing.
- Client/Server, Telecommunications, Intranets, and Extranets: An audit to verify that telecommunications controls are in place on the client (computer receiving services), server, and on the network connecting the clients and servers.
And some lump all IT audits as being one of only two type: 'general control review' audits or 'application control review' audits.
Itsm Audit Checklist
A number[who?] of IT audit professionals from the Information Assurance realm consider there to be three fundamental types of controls[disambiguation needed] regardless of the type of audit to be performed, especially in the IT realm. Many frameworks and standards try to break controls into different disciplines or arenas, terming them “Security Controls“, ”Access Controls“, “IA Controls” in an effort to define the types of controls involved. At a more fundamental level, these controls can be shown to consist of three types of fundamental controls: Protective/Preventative Controls, Detective Controls and Reactive/Corrective Controls.
In an IS, there are two types of auditors and audits: internal and external. IS auditing is usually a part of accounting internal auditing, and is frequently performed by corporate internal auditors. An external auditor reviews the findings of the internal audit as well as the inputs, processing and outputs of information systems. The external audit of information systems is frequently a part of the overall external auditing performed by a Certified Public Accountant (CPA) firm.[1]
IS auditing considers all the potential hazards and controls in information systems. It focuses on issues like operations, data, integrity, software applications, security, privacy, budgets and expenditures, cost control, and productivity. Guidelines are available to assist auditors in their jobs, such as those from Information Systems Audit and Control Association.[1]
IT audit process[edit]
The following are basic steps in performing the Information Technology Audit Process:[4]
- Planning IN
- Studying and Evaluating Controls
- Testing and Evaluating Controls
- Reporting
- Follow-up
- Reports
Information security[edit]
Auditing information security is a vital part of any IT audit and is often understood to be the primary purpose of an IT Audit. The broad scope of auditing information security includes such topics as data centers (the physical security of data centers and the logical security of databases, servers and network infrastructure components),[5]networks and application security. Like most technical realms, these topics are always evolving; IT auditors must constantly continue to expand their knowledge and understanding of the systems and environment& pursuit in system company.
History of IT auditing[edit]
The concept of IT auditing was formed in the mid-1960s. Since that time, IT auditing has gone through numerous changes, largely due to advances in technology and the incorporation of technology into business.
Currently, there are many IT-dependent companies that rely on information technology in order to operate their business e.g. Telecommunication or Banking company. For the other types of business, IT plays the big part of company including the applying of workflow instead of using the paper request form, using the application control instead of manual control which is more reliable or implementing the ERP application to facilitate the organization by using only 1 application. According to these, the importance of IT Audit is constantly increased. One of the most important roles of the IT audit is to audit over the critical system in order to support the financial audit or to support the specific regulations announced e.g. SOX.
Fatafati (Barfi).mp3. Apr 18, Nice song. Song Fatafati: Ranbir Kapoor sings for Anurag. Size of file. Free Download Fatafati (Barfi).mp3. Download lagu haddad alwi kaulah ibuku cinta kasihku.

Audit personnel[edit]
Professional certifications[edit]
- Certified Information Systems Auditor (CISA)
- Practitioner Certificate in Information Security Auditing (PCISA) [6]
- Certified Internal Auditor (CIA)
- Certified in Risk and Information Systems Control (CRISC)
- Certification and Accreditation Professional (CAP)
- Certified Computer Professional (CCP)
- Certified Information Privacy Professional (CIPP)
- Certified Information Systems Security Professional (CISSP)
- Certified Information Security Manager (CISM)
- Certified Public Accountant (CPA)
- Certified Internal Controls Auditor (CICA)
- Forensics Certified Public Accountant (FCPA)
- Certified Fraud Examiner (CFE)
- Certified Forensic Accountant (CrFA)
- Certified Commercial Professional Accountant (CCPA)
- Certified Accounts Executive (CEA)
- Certified Professional Internal Auditor (CPIA)
- Certified Professional Management Auditor (CPMA)
- Chartered Accountant (CA)
- Chartered Certified Accountant (ACCA/FCCA)
- GIAC Certified System & Network Auditor (GSNA)[7]
- Certified Information Technology Professional (CITP); to certify, auditors should have 3 years experience
- Certified e-Forensic Accounting Professional] (CFAP)[8]
- Certified ERP Audit Professional (CEAP)[9])
Principles of an IT audit[edit]
The following principles of an audit should find a reflection:[10]
- Timeliness: Only when the processes and programming is continuously inspected in regard to their potential susceptibility to faults and weaknesses, but as well with regard to the continuation of the analysis of the found strengths, or by comparative functional analysis with similar applications an updated frame can be continued.
- Source openness: It requires an explicit reference in the audit of encrypted programs, how the handling of open source has to be understood. E.g. programs, offering an open source application, but not considering the IM server as open source, have to be regarded as critical. An auditor should take an own position to the paradigm of the need of the open source nature within cryptologic applications.
- Elaborateness: Audit processes should be oriented to certain minimum standard. The recent audit processes of encrypting software often vary greatly in quality, in the scope and effectiveness and also experience in the media reception often differing perceptions. Because of the need of special knowledge on the one hand and to be able to read programming code and then on the other hand to also have knowledge of encryption procedures, many users even trust the shortest statements of formal confirmation. Individual commitment as an auditor, e.g. for quality, scale and effectiveness, is thus to be assessed reflexively for yourself and to be documented within the audit.
- The financial context: Further transparency is needed to clarify whether the software has been developed commercially and whether the audit was funded commercially (paid Audit). It makes a difference whether it is a private hobby / community project or whether a commercial company is behind it.
- Scientific referencing of learning perspectives: Each audit should describe the findings in detail within the context and also highlight progress and development needs constructively. An auditor is not the parent of the program, but at least he or she is in a role of a mentor, if the auditor is regarded as part of a PDCA learning circle (PDCA = Plan-Do-Check-Act). There should be next to the description of the detected vulnerabilities also a description of the innovative opportunities and the development of the potentials.
- Literature-inclusion: A reader should not rely solely on the results of one review, but also judge according to a loop of a management system (e.g. PDCA, see above), to ensure, that the development team or the reviewer was and is prepared to carry out further analysis, and also in the development and review process is open to learnings and to consider notes of others. A list of references should be accompanied in each case of an audit.
- Inclusion of user manuals & documentation: Further a check should be done, whether there are manuals and technical documentations, and, if these are expanded.
- Identify references to innovations: Applications that allow both, messaging to offline and online contacts, so considering chat and e-mail in one application - as it is also the case with GoldBug - should be tested with high priority (criterion of presence chats in addition to the e-mail function). The auditor should also highlight the references to innovations and underpin further research and development needs.
This list of audit principles for crypto applications describes - beyond the methods of technical analysis - particularly core values, that should be taken into account
Emerging issues[edit]
There are also new audits being imposed by various standard boards which are required to be performed, depending upon the audited organization, which will affect IT and ensure that IT departments are performing certain functions and controls appropriately to be considered compliant. Examples of such audits are SSAE 16, ISAE 3402, and ISO27001:2013.
Web presence audits[edit]
The extension of the corporate IT presence beyond the corporate firewall (e.g. the adoption of social media by the enterprise along with the proliferation of cloud-based tools like social media management systems) has elevated the importance of incorporating web presence audits into the IT/IS audit. The purposes of these audits include ensuring the company is taking the necessary steps to:
- rein in use of unauthorized tools (e.g. 'shadow IT')
- minimize damage to reputation
- maintain regulatory compliance
- prevent information leakage
- mitigate third-party risk
- minimize governance risk[11][12]
The use of departmental or user developed tools has been a controversial topic in the past. However, with the widespread availability of data analytics tools, dashboards, and statistical packages users no longer need to stand in line waiting for IT resources to fullfill seemingly endless requests for reports. The task of IT is to work with business groups to make authorized access and reporting as straightforward as possible. To use a simple example, users should not have to do their own data matching so that pure relational tables are linked in a meaningful way. IT needs to make non-normalized, data warehouse type files available to users so that their analysis work is simplified. For example, some organizations will refresh a warehouse periodically and create easy to use 'flat' tables which can be easily uploaded by a package such as Tableau and used to create dashboards.
Enterprise communications audits[edit]
The rise of VOIP networks and issues like BYOD and the increasing capabilities of modern enterprise telephony systems causes increased risk of critical telephony infrastructure being misconfigured, leaving the enterprise open to the possibility of communications fraud or reduced system stability. Banks, financial institutions, and contact centers typically set up policies to be enforced across their communications systems. The task of auditing that the communications systems are in compliance with the policy falls on specialized telecom auditors. These audits ensure that the company's communication systems:
- adhere to stated policy
- follow policies designed to minimize the risk of hacking or phreaking
- maintain regulatory compliance
- prevent or minimize toll fraud
- mitigate third-party risk
- minimize governance risk[13][14]
Enterprise communications audits are also called voice audits,[15] but the term is increasingly deprecated as communications infrastructure increasingly becomes[16] is also deprecated because modern communications infrastructure, especially when dealing with customers, is omni-channel, where interaction takes place across multiple channels, not just over the telephone.[17]One of the key issues that plagues enterprise communication audits is the lack of industry-defined or government-approved standards. IT audits are built on the basis of adherence to standards and policies published by organizations such as NIST and PCI, but the absence of such standards for enterprise communications audits means that these audits have to be based an organization's internal standards and policies, rather than industry standards. As a result, enterprise communications audits are still manually done, with random sampling checks. Policy Audit Automation tools for enterprise communications have only recently become available.[18]
See also[edit]
Computer forensics[edit]
Operations[edit]
Miscellaneous[edit]
Irregularities and illegal acts[edit]

- AICPA Standard: SAS 99 Consideration of Fraud in a Financial Statement Audit
References[edit]
- ^ abcRainer, R. Kelly, and Casey G. Cegielski. Introduction to information systems. 3rd ed. Hoboken, N.J.: Wiley ;, 2011. Print.
- ^Richard A. Goodman; Michael W. Lawless (1994). Technology and strategy: conceptual models and diagnostics. Oxford University Press US. ISBN978-0-19-507949-4. Retrieved May 9, 2010.
- ^K. Julisch et al., Compliance by Design – Bridging the Chasm between Auditors and IT Architects. Computers & Security, Elsevier. Volume 30, Issue 6-7, Sep.-Oct. 2011.
- ^Davis, Robert E. (2005). IT Auditing: An Adaptive Process. Mission Viejo: Pleier Corporation. ISBN978-0974302997.
- ^'Advanced System, Network and Perimeter Auditing'.
- ^'IISP accredited certification'(PDF).
- ^'GIAC GSNA Information'.
- ^http://www.iacae.org/English/Certification/CFAP.php
- ^ICAEA, 'Certification Program', http://www.iacae.org/English/Certification/CEAP.php
- ^References to further core audit principles, in: Adams, David / Maier, Ann-Kathrin (2016): BIG SEVEN Study, open source crypto-messengers to be compared - or: Comprehensive Confidentiality Review & Audit of GoldBug, Encrypting E-Mail-Client & Secure Instant Messenger, Descriptions, tests and analysis reviews of 20 functions of the application GoldBug based on the essential fields and methods of evaluation of the 8 major international audit manuals for IT security investigations including 38 figures and 87 tables., URL: https://sf.net/projects/goldbug/files/bigseven-crypto-audit.pdf - English / German Language, Version 1.1, 305 pages, June 2016 (ISBN: DNB 110368003X - 2016B14779)
- ^Juergens, Michael. 'Social Media Risks Create an Expanded Role for Internal Audit'. Wall Street Journal. Retrieved 10 August 2015.
- ^'Social Media Audit/Assurance Program'. ISACA. ISACA. Retrieved 10 August 2015.
- ^Lingo, Steve. 'A Communications Audit: The First Step on the Way to Unified Communications'. The XO Blog. Retrieved 17 Jan 2016.
- ^'Telephone System Audit Service'. 1st Communications Services. 1st Communications Services.
- ^'Voice Audit'. www.securelogix.com. Retrieved 2016-01-20.
- ^'IP Telephony Design and Audit Guidelines'(PDF). www.eurotelecom.ro.
- ^'What is omnichannel? - Definition from WhatIs.com'. SearchCIO. Retrieved 2016-01-20.
- ^'Assertion'. SmarterHi Communications. Retrieved 2016-01-21.
External links[edit]
- A career as Information Systems Auditor, by Avinash Kadam (Network Magazine)
- Federal Financial Institutions Examination Council (FFIEC)
- American Institute of Certified Public Accountants (AICPA)
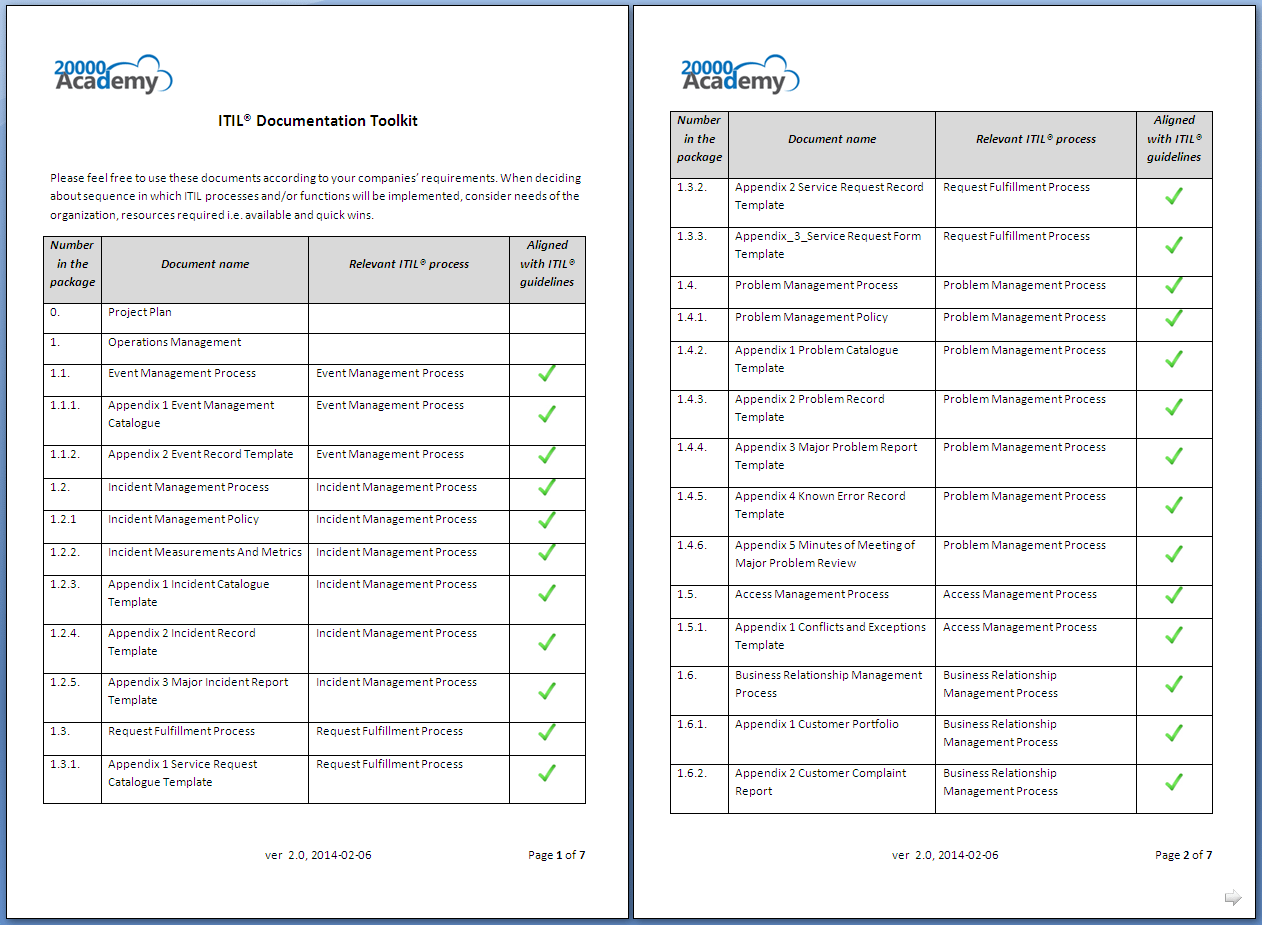
- IT Services Library (ITIL)
A data center can face many different audits, from security procedures to energy efficiency. Typically, auditors focus on one single aspect every year if audits are annual. Because so many different aspects of a data center audit exist, no single standard covers them all; however, companies can adhere to standards that cover individual aspects.
ITIL Checklists
The Information Technology Infrastructure Library provides a set of checklists for various aspects of service development and management, which apply to data centers. In particular, the Service Delivery and Information Technology and Communications Infrastructure sections of ITIL apply do data centers. ITIL is an industry standard, and common for management and planning of information technology projects in Europe.
Security Audit using ISO 27000
Verifying the security of any organization can be problematic, and data centers are no exception. International Organization of Standardization/International Electrotechnical Commission 27000 series is a set of standards that specify how to use information security systems. In particular, one of the intended uses is to provide relevant information about information security policies, directives, standards and procedures to external organizations.
Outsourcing Services Audit using ISO 27001
The ISO 27001 contains checklists for data center outsourcing services audits. The points for verification include the installation and operations of hardware and software; the continuous monitoring of performance, capacity and operational status; and software management practices, including backup and upgrade. Recovery procedures in the event of failure and the capabilities to support outsourced services are also part of the checklist.
SAS 70 audit of Service Organizations
The American Institute of Certified Public Accountants developed the Statement on Auditing Standards No. 70 for service organizations. It is a means of verifying the control objectives and control activities of a service organization. In case of IT-related services, this implies a data center audit. Despite the common use of the SAS 70, the Statement on Standards for Attestation Engagements number 16 and the audit standard Audit Considerations Relating to an Entity Using a Service Organization replaced it. While neither the SAS 70 nor the new standards replacing it contains checklists as such, they aim to provide a set of requirements that you can check.
- scanrail/iStock/Getty Images